Six of the Worst Ransomware Attacks in 2017

Ransomware has cemented its place as one of the biggest threats to security today. The number of emails infected with ransomware attacks rose by an enormous 6,000 percent from 2016 to 2017.
Research suggests that ransomware attackers are gradually moving away from high volume mass campaigns to targeted and customised attacks, aimed at larger companies with more money. However, no industry, organisation or individual is immune to the threat of ransomware: a business is attacked by ransomware every 40 seconds, while an individual is attacked every 10.
To make matters worse, the average ransom demand has increased in price by three times since 2015 and now sits at over $1,000. Because it’s impossible to be 100 percent secure from malware, it’s as important as ever to remain vigilant and aware of the potential dangers you could be facing online.
This recap of 2017’s worst ransomware attacks serves as a reminder of the dangers of cyber attacks — are you ready for what awaits in 2018?
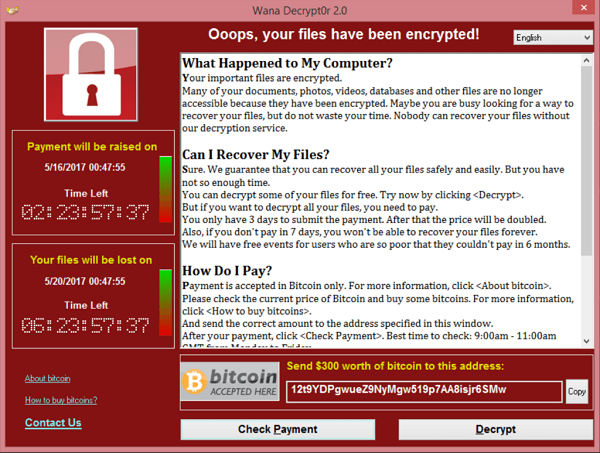
WannaCry
WannaCry was a form of ransomware that exploited a flaw in Windows’ Server Message Block (SMB) protocol. Once it infected the system, WannaCry encrypted files on the machine and forced its owner to pay the attacker in Bitcoin for the decryption key.
WannaCry was the first ransomware to affect the entire world, infecting hundreds of thousands of machines in one day. Its consequences were particularly felt in China, Russia and India, where banks, public transport systems, hospitals and universities were affected. Some reports say that the damage caused by WannaCry could be as high as $4 billion.
The ransomware targeted Windows systems that lacked a security update from March 2017, which acts as an important reminder of the need for better security practices.
NotPetya
About a month after WannaCry, NotPetya was the next large-scale ransomware attack to hit the web. NotPetya started as a fake tax software update that infected countless computers in over 100 countries in just a few days. The code used to build NotPetya was not designed to extort money from its victims, but rather to destroy everything in its path.
The ransomware affected American pharmaceutical company Merck — which cost them over $300 million alone — as well as Danish shipping company Maersk, Russian oil corporation Rosnoft and FedEx. It hit Ukraine’s infrastructure especially hard, disrupting utilities including power plants, airports, public transport, supermarkets and the central bank.
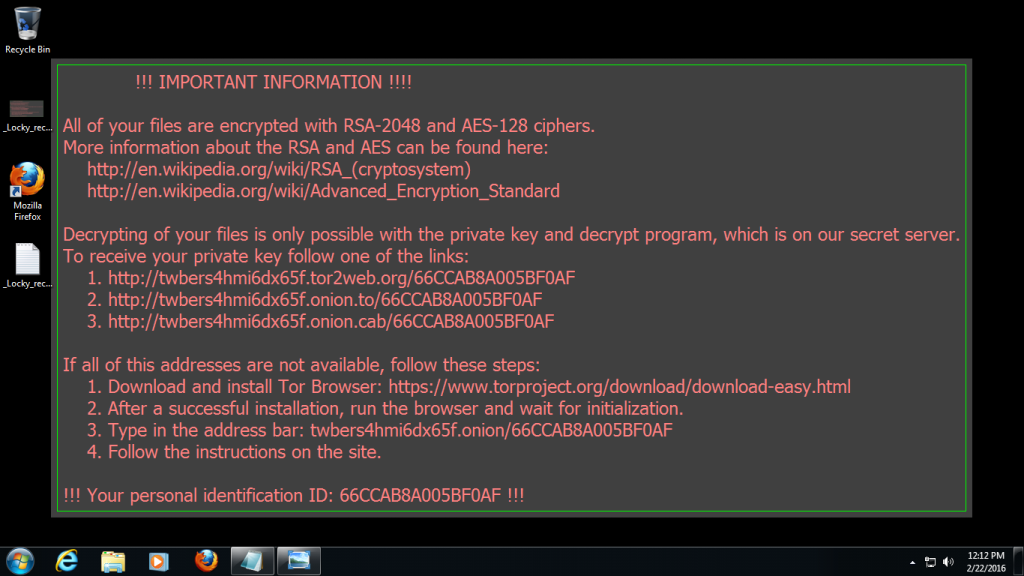
Locky
Locky was a phishing scam that originated in 2016, but made a return with new forms Lukitus and Diablo in 2017. The malware was sent as a zipped attachment with malicious JavaScript via email, masquerading as invoices from companies such as Amazon Marketplace and Herbalife.
Crowned the king of spam emails, Locky could reach millions of users per day. One of the first organisations affected was the Hollywood Presbyterian Medical Centre in Los Angeles. The hospital was forced to pay a ransom of 40 Bitcoin (approximately $17,000 at the time) to regain access to its systems.
Typically, the requested ransom amount was 0.5 to 1 Bitcoin.
CrySis
CrySis was a Remote Desktop Protocol (RDP) compromise, typically installed by hacking a machine and manually installing the ransomware. An RDP compromise is one of the most common ways to deploy ransomware because cybercriminals can compensate admin accounts and systems that control entire organisations.
It started in Australia and New Zealand before moving to hit organisations across the globe, targeting the American healthcare sector in particular. To make it worse, as well as encrypting a computer, CrySis removed all automatic backups so that users couldn’t access them to restore files.
Jaff
Jaff was part of a ransomware family active since 2015. Heavily mimicking Locky’s tactics, the ransomware was spread via fake shipping invoices sent through email.
Once an infected attachment was opened, Jaff would download malware and encrypt the machine’s files in typical ransomware style. Those affected received a ransom note demanding 1.79 Bitcoin — equivalent to $4,000 at the time — in exchange for the safe return of their files.
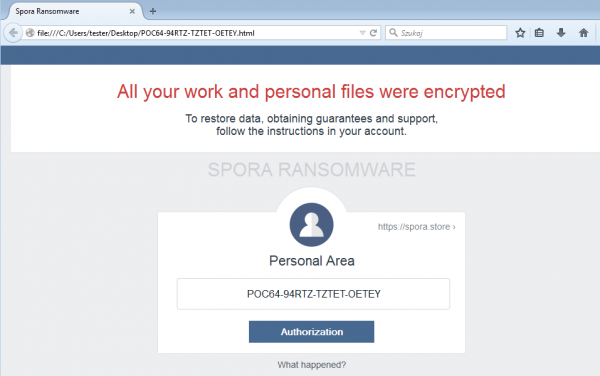
Spora
Spora was distributed either via spam emails containing a HTA file, or through phishing links. It targeted all versions of Windows. Usually, the emails were branded as a major company, a shipment notification, or an invoice (once again, the similarities to Jaff and Locky are evident).
Once deployed, Spora ran silently and encrypted files with selected extensions. Upon being infected, the user was linked to a website with four payment options. The user would then have to choose an option and send money via BitCoin to receive the decryption key for their files.

Notice: Undefined variable: commenter in /var/www/siteguard_prod/blog/wp-content/themes/siteguardblog/template-parts/post/content.php on line 70
Notice: Undefined variable: aria_req in /var/www/siteguard_prod/blog/wp-content/themes/siteguardblog/template-parts/post/content.php on line 70
Notice: Undefined variable: html_req in /var/www/siteguard_prod/blog/wp-content/themes/siteguardblog/template-parts/post/content.php on line 70
Notice: Undefined variable: html5 in /var/www/siteguard_prod/blog/wp-content/themes/siteguardblog/template-parts/post/content.php on line 71
Notice: Undefined variable: commenter in /var/www/siteguard_prod/blog/wp-content/themes/siteguardblog/template-parts/post/content.php on line 71
Notice: Undefined variable: aria_req in /var/www/siteguard_prod/blog/wp-content/themes/siteguardblog/template-parts/post/content.php on line 71
Notice: Undefined variable: html_req in /var/www/siteguard_prod/blog/wp-content/themes/siteguardblog/template-parts/post/content.php on line 71
Notice: Undefined variable: html5 in /var/www/siteguard_prod/blog/wp-content/themes/siteguardblog/template-parts/post/content.php on line 72
Notice: Undefined variable: commenter in /var/www/siteguard_prod/blog/wp-content/themes/siteguardblog/template-parts/post/content.php on line 72
Notice: Undefined variable: post_id in /var/www/siteguard_prod/blog/wp-content/themes/siteguardblog/template-parts/post/content.php on line 77
Notice: Undefined variable: user_identity in /var/www/siteguard_prod/blog/wp-content/themes/siteguardblog/template-parts/post/content.php on line 82
Notice: Undefined variable: user_identity in /var/www/siteguard_prod/blog/wp-content/themes/siteguardblog/template-parts/post/content.php on line 83
Notice: Undefined variable: post_id in /var/www/siteguard_prod/blog/wp-content/themes/siteguardblog/template-parts/post/content.php on line 84